Network Tasks 🏭
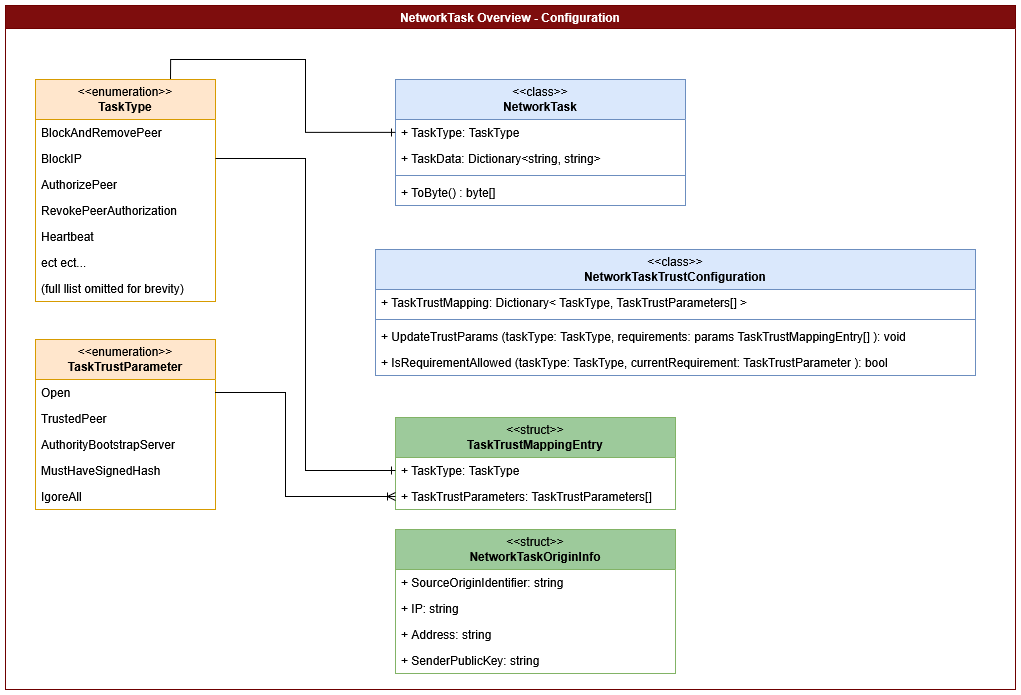
Network tasks represent discrete actions carried out across the peer-to-peer network, such as blocking, messaging, or synchronizing data. Each task is described by a NetworkTask object, which contains:
- TaskType: An enum value indicating the exact operation (e.g.,
BlockIP,SendData, orAuthorizePeer). - TaskData: A dictionary holding any supporting information (e.g., target peer identifier, a message payload).
Task Flow
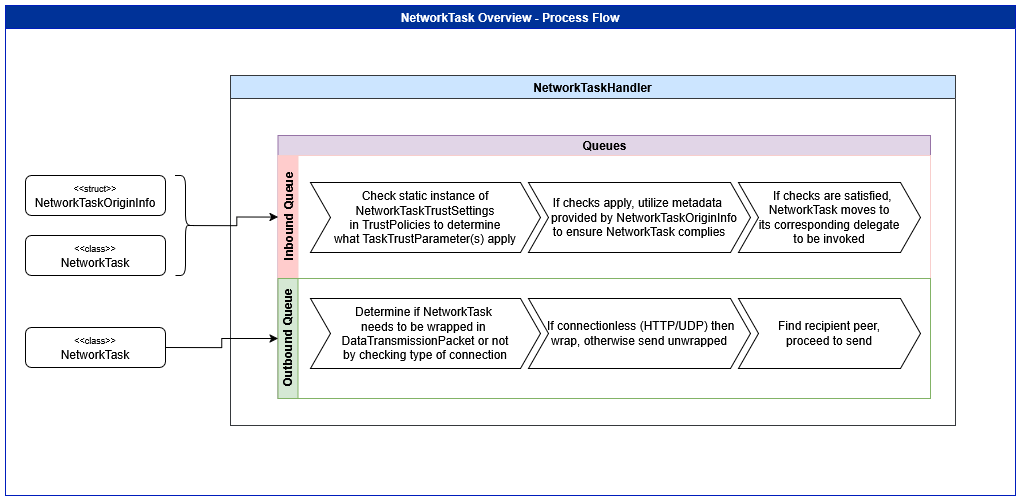
Tasks queue within the NetworkTaskHandler move in two directions:
Inbound Queue
When a peer sends aNetworkTask, it is placed in the inbound queue for validation. TheNetworkTaskOriginInfoprovides metadata such as the sender’s IP address, SourceOriginIdentifier of the packet it came from, or a public key if known. TheNetworkTaskTrustConfiguration(exposed asNetworkTaskTrustSettingswithinPeerNetwork.TrustPolicies.PeerNetworkTrustPolicies) applies trust rules—if a task fails to comply, it is blocked; otherwise it is routed to the corresponding handler delegate and executed.Outbound Queue
Locally created tasks (e.g., to send a message or request data) go into the outbound queue. Before dispatching, the system checks whether the connection requires wrapping the task in a higher-levelDataTransmissionPacketor can send it directly. Typically, connectionless transmission is wrapped (e.g. UDP or HTTP)
Trust Configuration
NetworkTaskTrustConfiguration maps each TaskType to a set of required TaskTrustParameter values. These parameters (e.g., Open, TrustedPeer, or AuthorityBootstrapServer) define which security checks, if any, must be conducted to ensure the NetworkTask complies with security standards. This system lets developers tailor how strictly each task is authenticated or whether it needs a signed hash.
Handlers and Delegates
NetworkTaskHandler houses default delegate methods for each TaskType (e.g., DefaultSendMessageHandler). You can override these delegates to implement custom logic. Valid tasks are handed to their respective delegate, which performs the corresponding action (block, authorize, send data, ect).
This approach ensures that each task is processed securely and in a consistent, extensible manner.